This is the 4th part of my blog series on the Road to CE series. We’ll be starting to look at the technical controls inside of AAD and Intune to assist with Cyber Essentials. Please note I’ll be specifically talking about AAD and Intune.
As previous stated under Cyber Essentials you need to know the make and OS version connecting to corporate data and excluding students. With that in mind, we (Jisc) took the decision to block personal (BYOD) Windows and Mac devices from connecting to our systems, this dramatically simplified things. This may change in the future but Windows Information Protection (the Windows BYOD tech) has been deprecated, the replacement isn’t ready yet.
These instructions will also use Mobile Application Management (MAM).
Intune enrolment restrictions
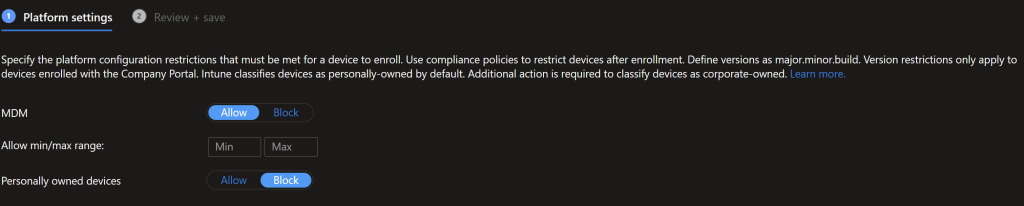
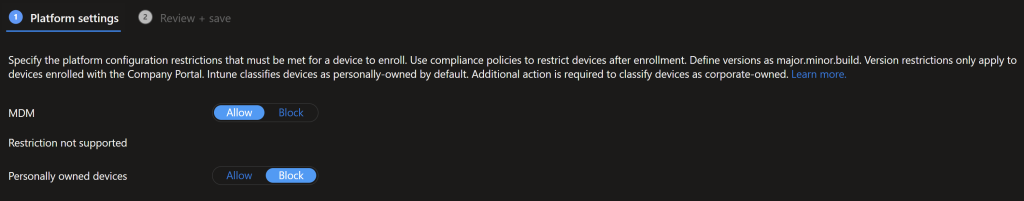
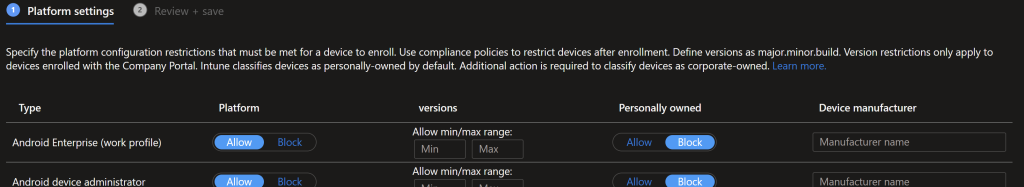
In Intune go to Devices > Device Enrollment > Enrollment device platform restrictions and configure it so personal devices are blocked from Enrolling into Intune, including iOS/Android. I’ll talk about that next.
If you need BYOD for Students or for doing a pilot you’ll create new policies, otherwise edit the All users policy. Configure these policies to block personal enrolment.

Next is the magic bit, Application Protection Policies.
Mobile Application Management
MAM will allow your users to register devices and isolate corporate data on those devices. You can then wipe that data without effecting the rest of the device. The big thing with MAM is the information you get from devices to ensure Cyber Essentials compliance.
We’ll be configuring Android and iOS with compliance policies.
Go to Apps > App protection policies and create a new Android policy. If you are using the Jisc CE Device Database include “Cyber Essentials” in the description.
Microsoft has a list of apps which are Supported Microsoft Intune apps | Microsoft Learn, if an app isn’t in the list contact your app maker to make the app support it, or if it’s an app you control you can wrap it to support Intune.
Web Apps can also be excluded if you want, we do this for our HR system to allow for downloading/access to payslips etc. (This may change).
Android MAM
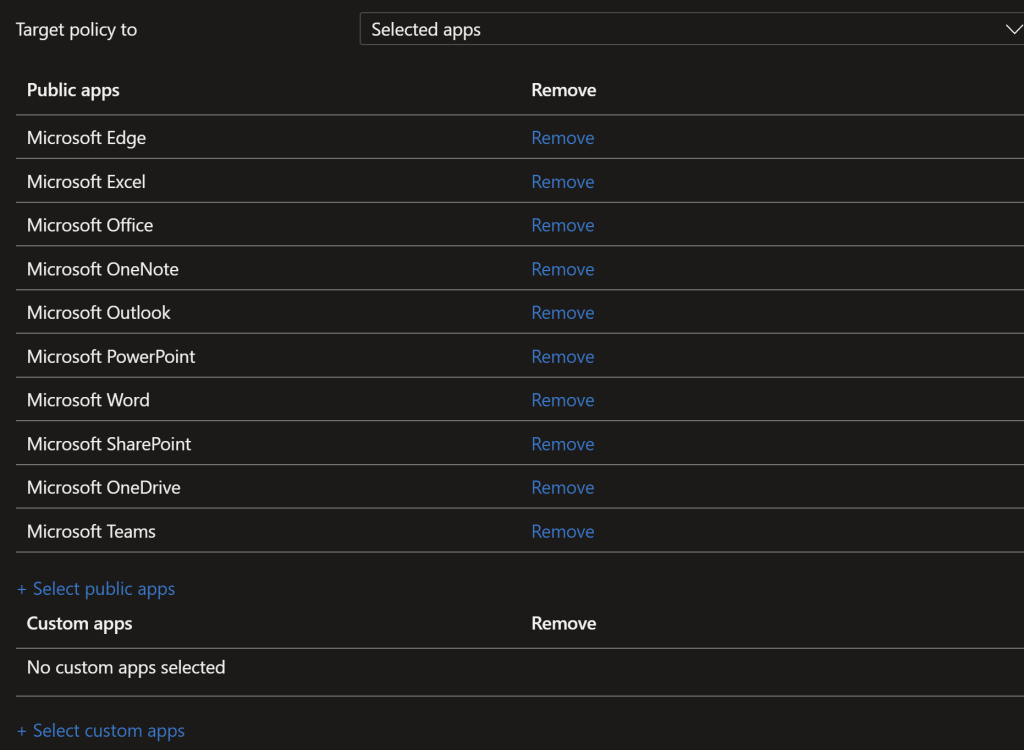
Target just unmanaged devices (toggle “Target to apps on all device types” to no).
Jisc just allows Microsoft core applications in here, but you add the apps that support.
Android Data Protection
Onto the Data Protection settings, Jisc has elected to lock this down a bit to avoid data leakage/isolation. We restrict copying files to OneDrive/SharePoint only and uploading data is only from OneDrive/SharePoint/Camera/Photo Gallery
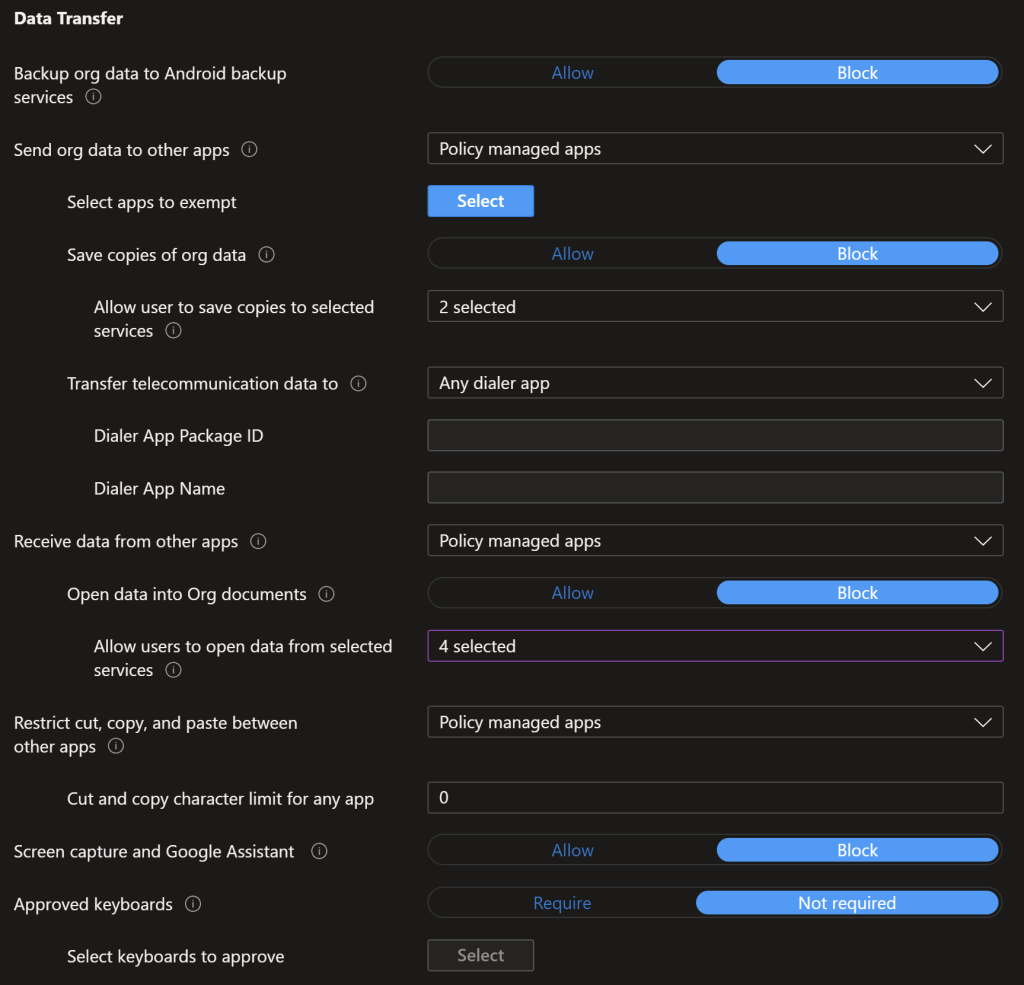
Then for encryption, we enforce encrypting org data, block printing and only block org data, not the whole device. Restricting the web to Microsoft Edge ensure the data is encrypted and the correct device compliance data is passed through to AAD. Microsoft Tunnel is a Intune Plan 2 feature.
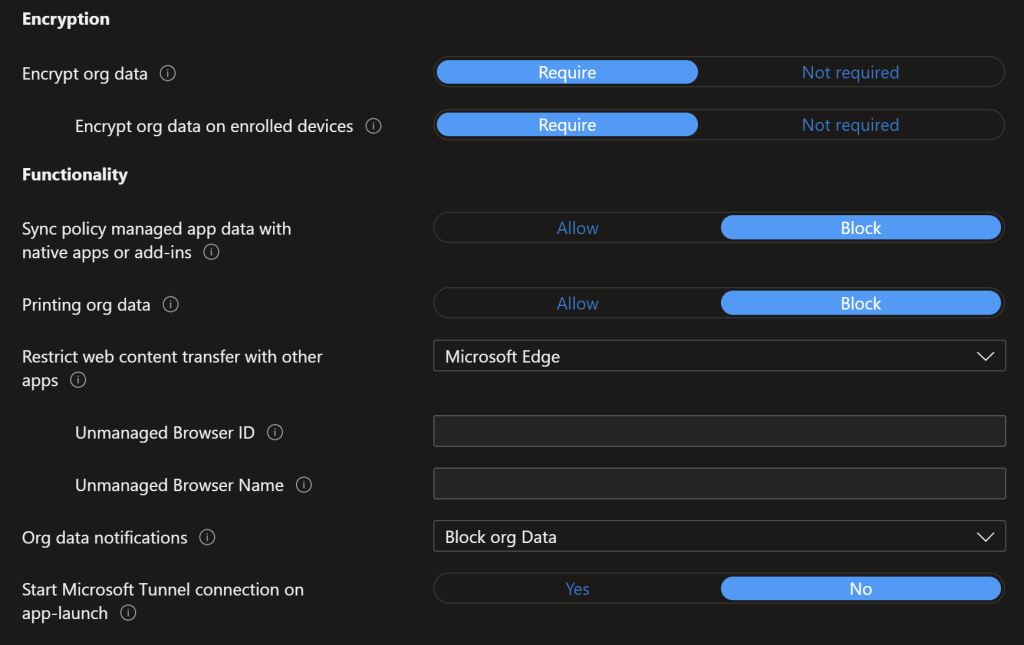
Android Access Requirements
Access requirements is where we set the CE compliance for data/device access. A PIN is required, this is entered every 24 hours, with biometric every 30 minutes.
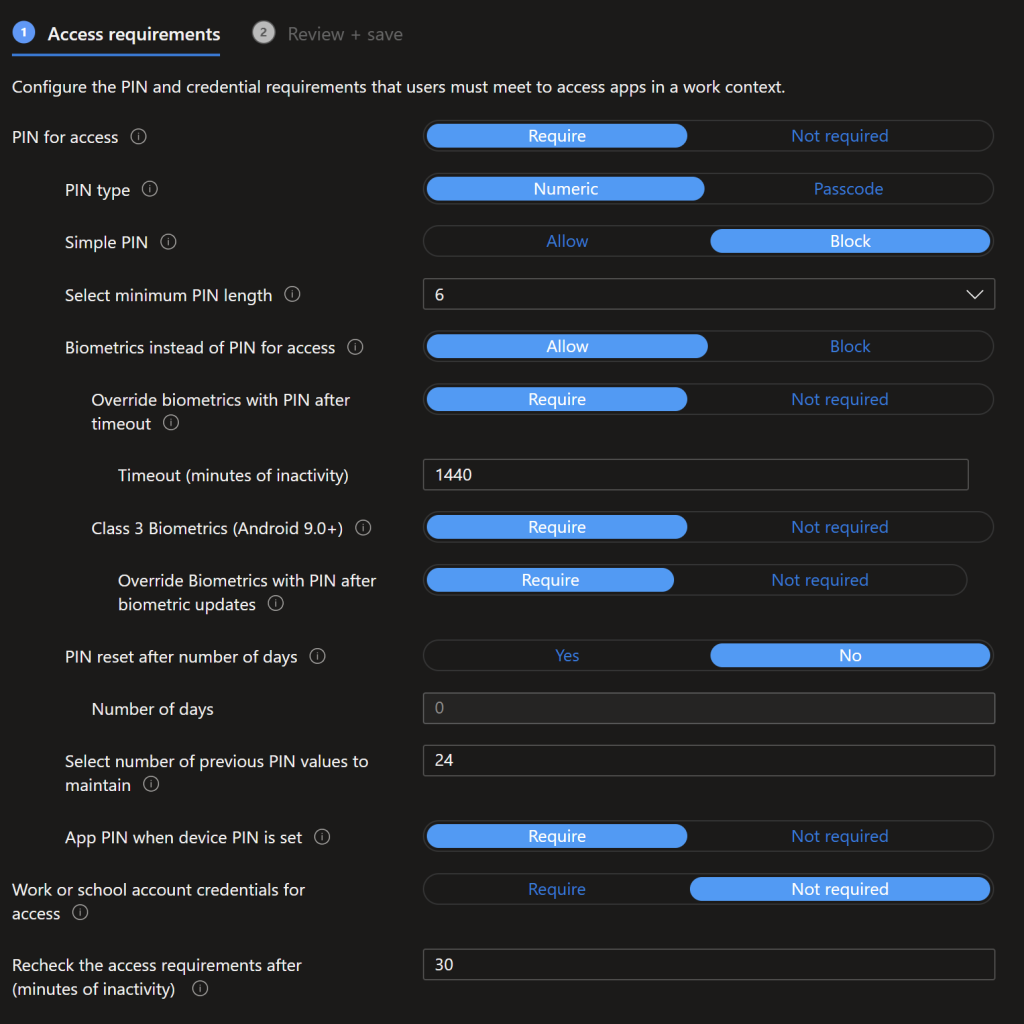
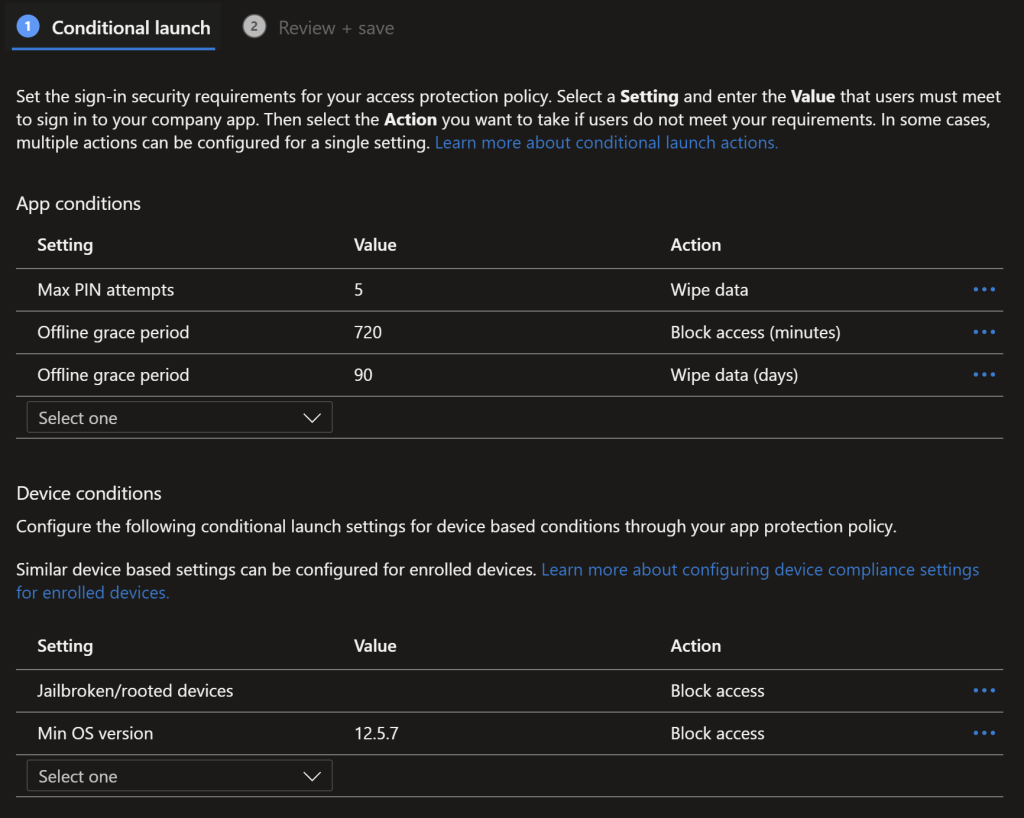
Android Conditional Launch Restrictions
Conditional Launch restrictions are the key here to CE compliance, data access is blocked for Rooted/Jailbroken devices, and the Min OS version and patch level is set. The Jisc CE Device Database tool will update these conditional launch settings for you, otherwise you’ll need a process to update these settings.
iOS MAM
iOS follows much the same policies as Android, set the device target all to no and select device types of unmanaged. On the apps select the Microsoft apps you want to configure/enforce compliance.
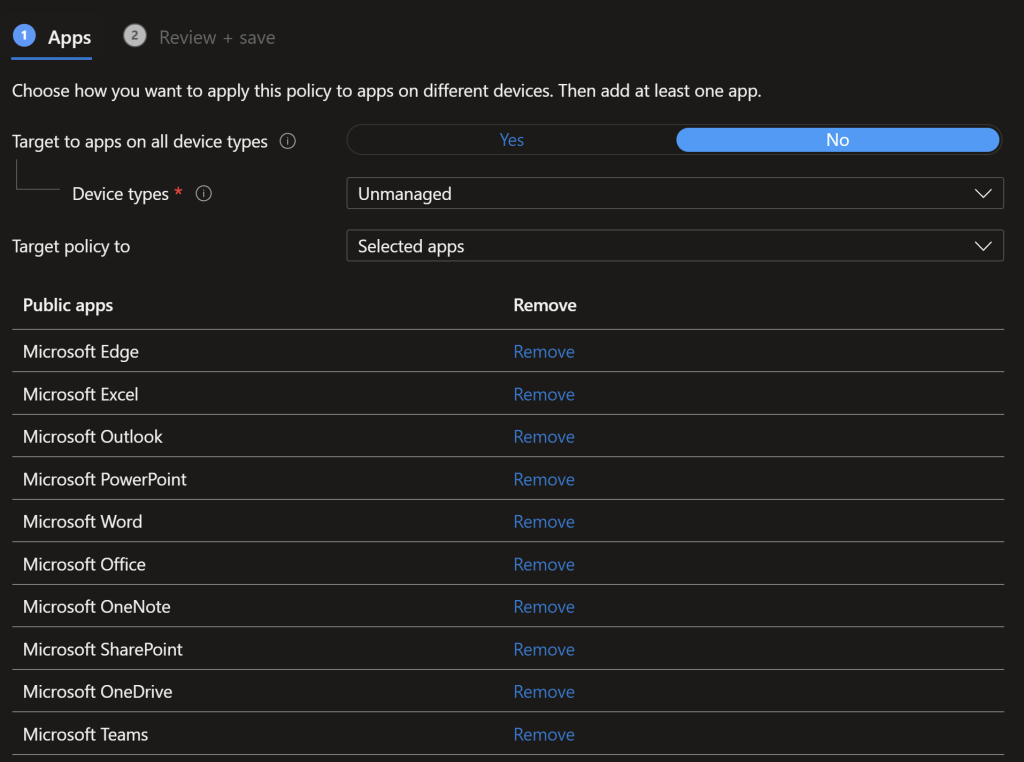
iOS Data Protection > Transfer
When you select Policy managed apps the exemptions are prefilled, if they aren’t refer to Microsoft’s docs. The exemptions basically say for certain urls it’s ok to open in the unmanaged app, or others they need to open in an Intune wrapped and managed app.
We only use OneDrive/SharePoint for filestore at Jisc so we only select that as a save location. Allowing the use of the Camera is optional, it’s useful to turn on especially in teams if you want to quickly take a picture of something and IM it to a colleague. We don’t allow attaching files outside of OneDrive/SharePoint/Camera however. This policy also prevents easily exfiltrating of data.
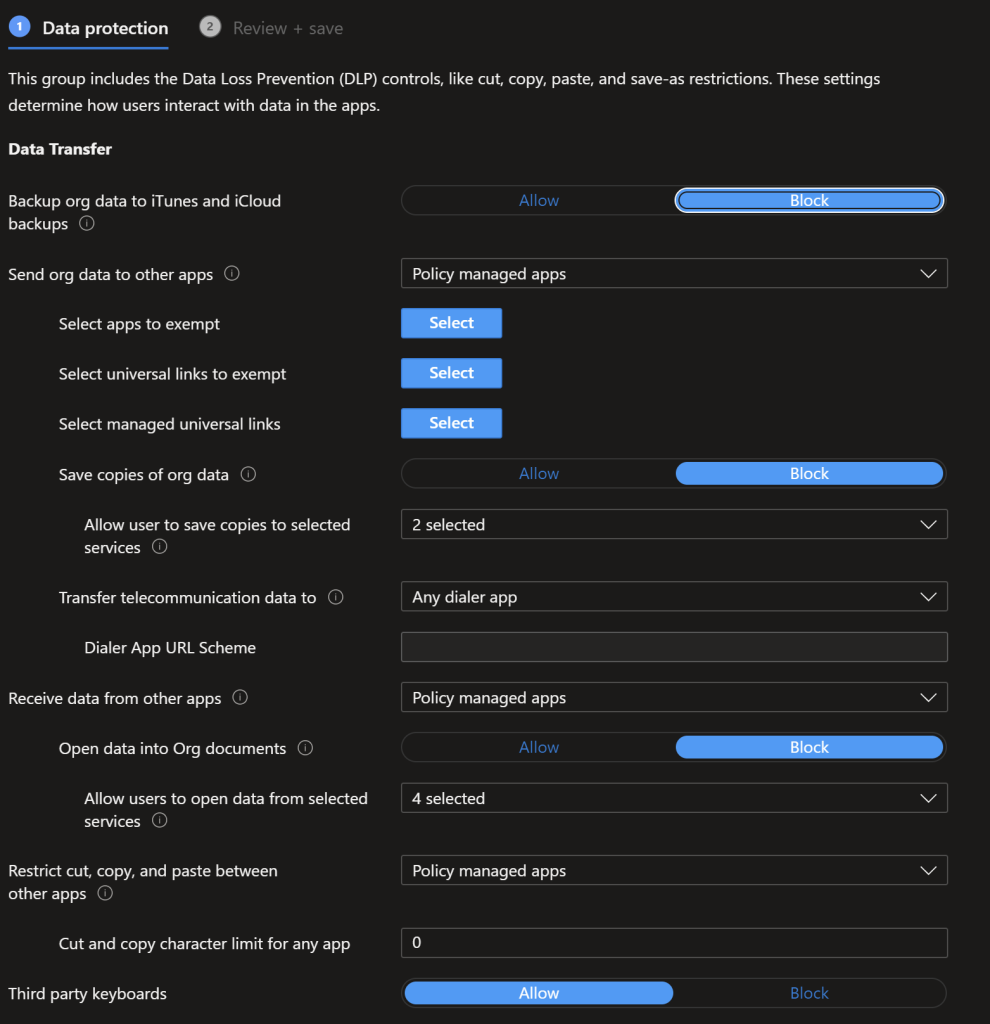
iOS Encryption/functionality settings
We enforce org data being isolated and encrypted in this section, disable syncing of data to the local device, block printing, require the use of Microsoft Edge for web content (Edge can be Intune controlled) and when the device is out of compliance block the org data.
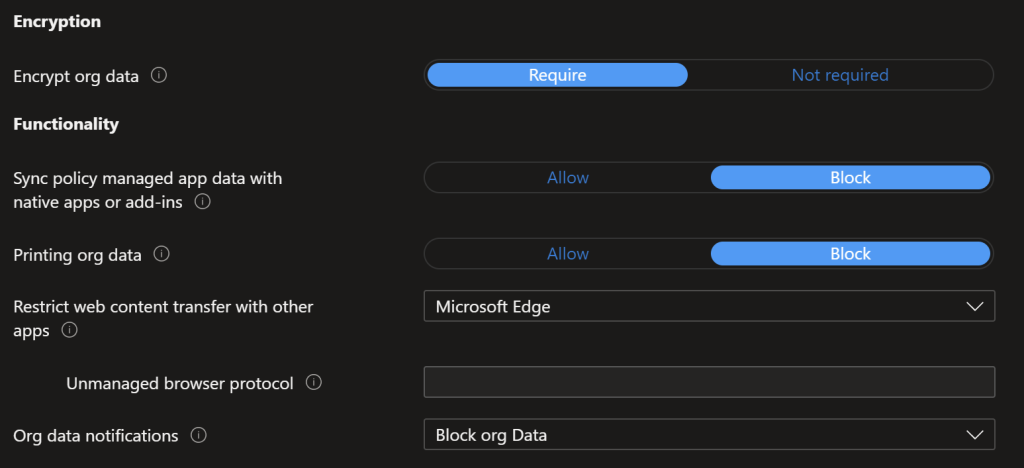
iOS Access Requirements
As with Android, we specify the minimum levels under Cyber Essentials in this section, you may want higher however. As with Android we set that we require PIN/Face ID every 24 hours with a check every 30 minutes.
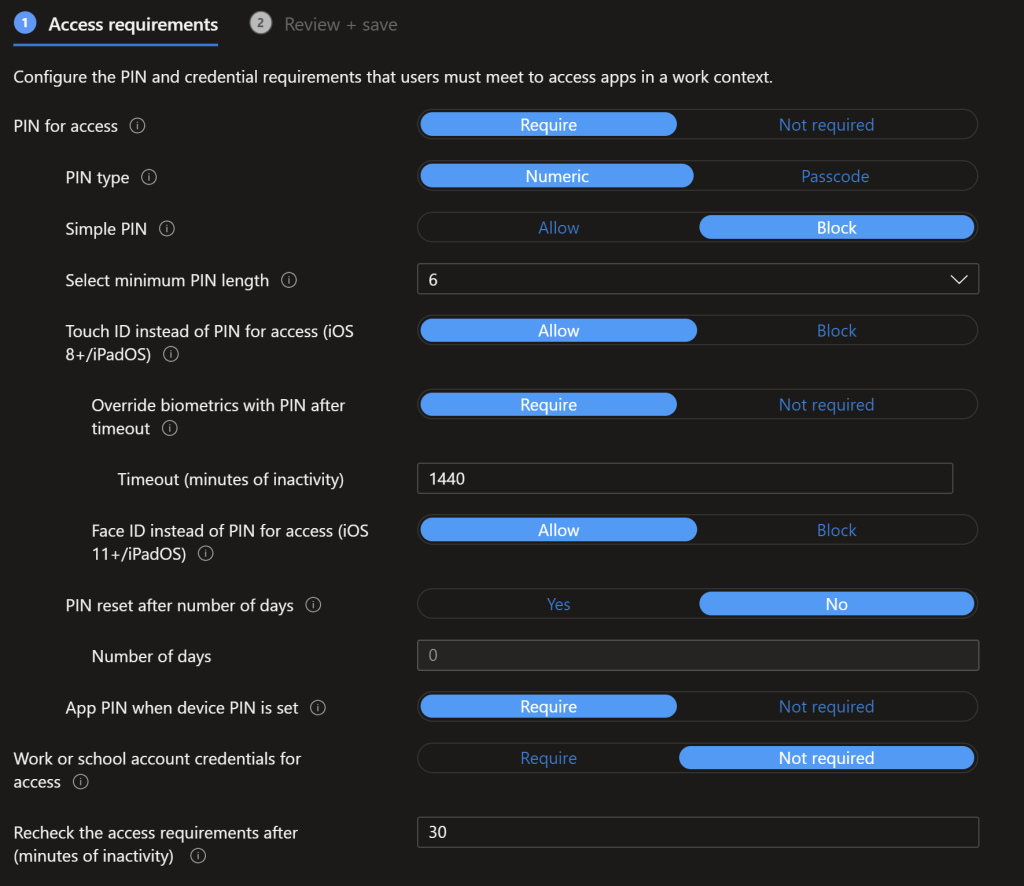
iOS Conditional Launch Conditions
We’re going to follow NCSC/Cyber Essentials guidance again with the conditional launch conditions, max pin attempts of 5, offline grace period of 12 hours after which the data is blocked and a further 90 days before the data is wiped off the device.
This is where we block access to data for jailbroken/rooted iOS devices and specify a min OS version for iOS. You should update this based on Apple’s guidance, the Jisc CE Device Database will do this automatically for you if “Cyber Essentials” is included in the policy description.
AAD Conditional Access Policies
The final step to enforce this is to use AAD Conditional Access to prevent access via any other means.
BYOD Non Permitted Devices
This policy blocks unmanaged devices with intune as the exclusion
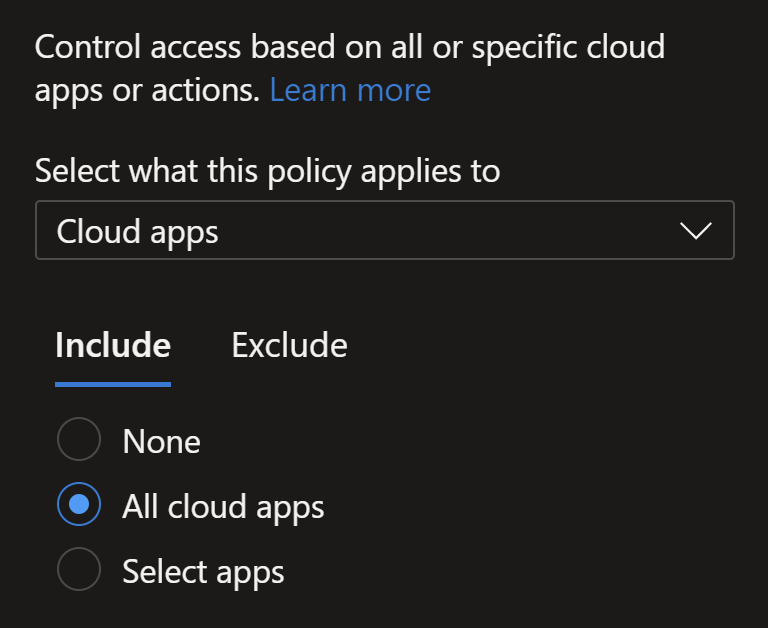
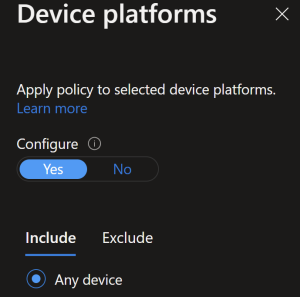
On Conditions you need to apply this policy to non iOS and Android devices.
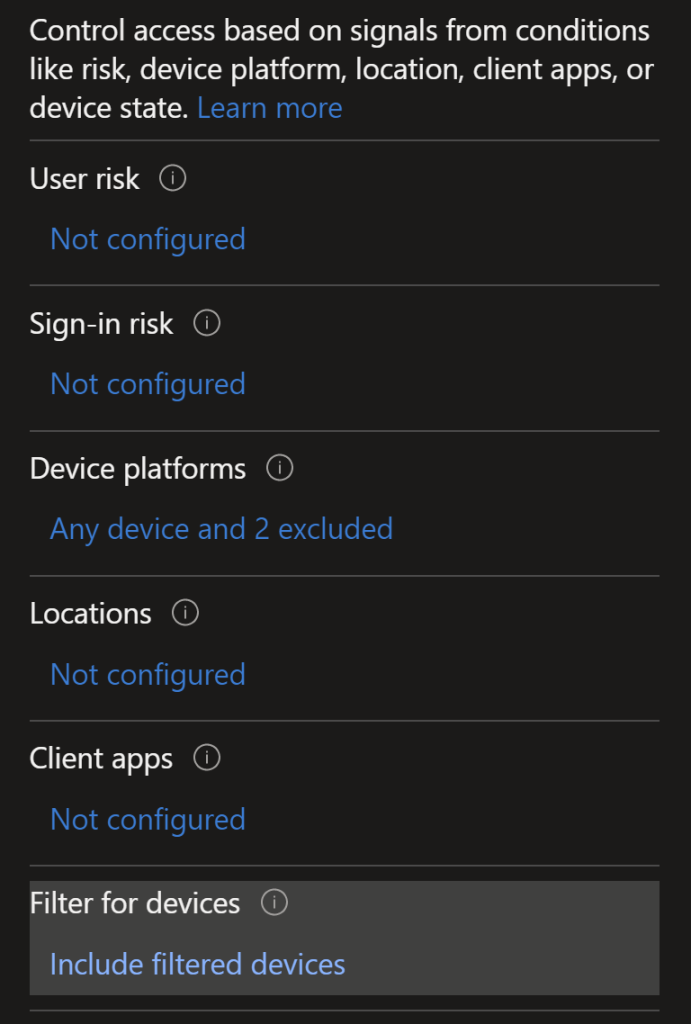
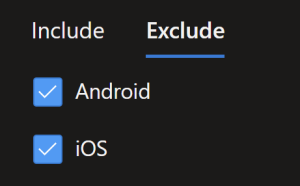
We’ll also filter out corporate devices from having this policy applied via a double negative filter on the device Ownership
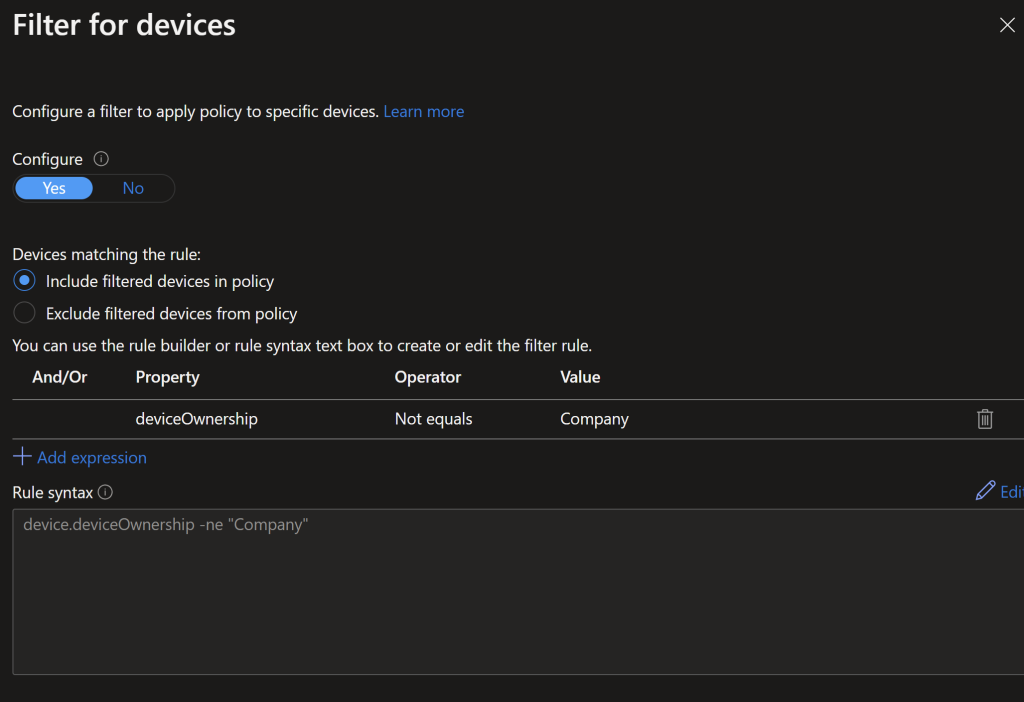
Finally the grant is set to Block Access.
BYOD permitted Apps
The other conditional access policy for BYOD will allow the permitted apps on compliant devices.
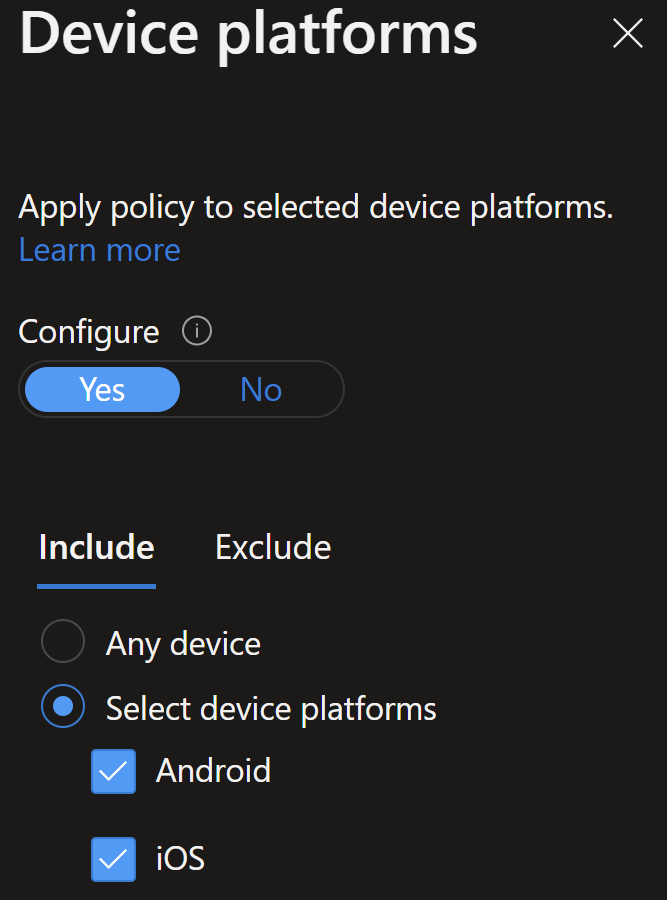
All cloud apps are in scope for this, you may want to exclude certain apps.
Where as the previous CA policy this one is will target explicitly iOS/Android devices.
We are doing the same filter as the previous policy to filter out corporate owned devices.
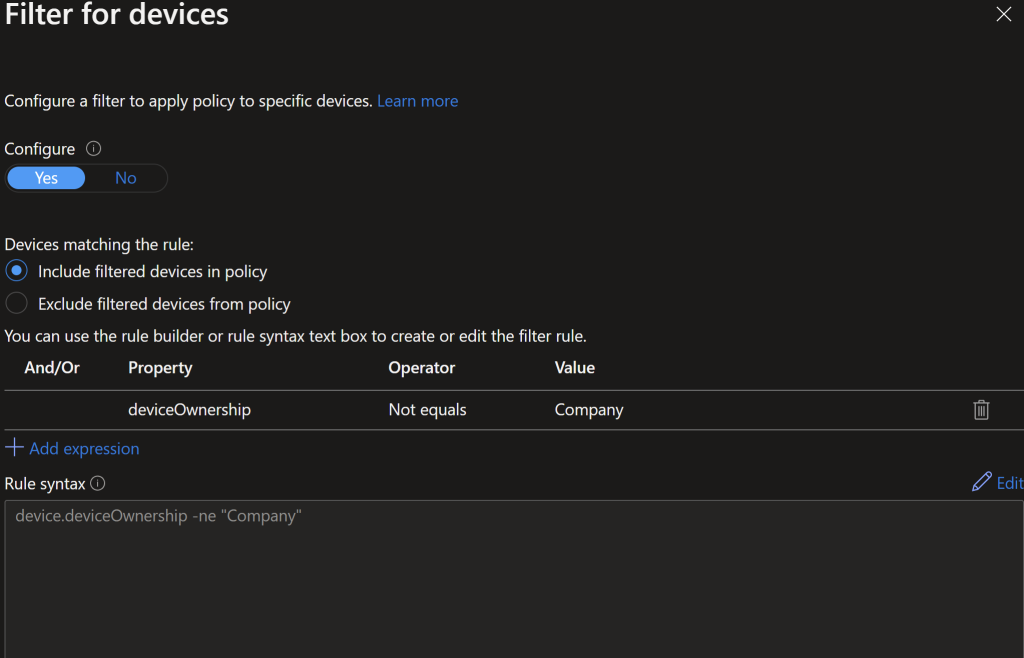
We have 2 conditions for a grant access: Require approved client app and Require app protection policy. This will enforce the app goes via the app protection policy. We also require both of these requirements.
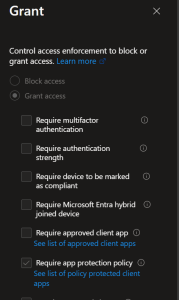
End user Experience
So what does this look like for the end user? Users will be asked to install Company Portal (this may change in the future on Android, already not required on iOS), after this the device will be checked for compliance.
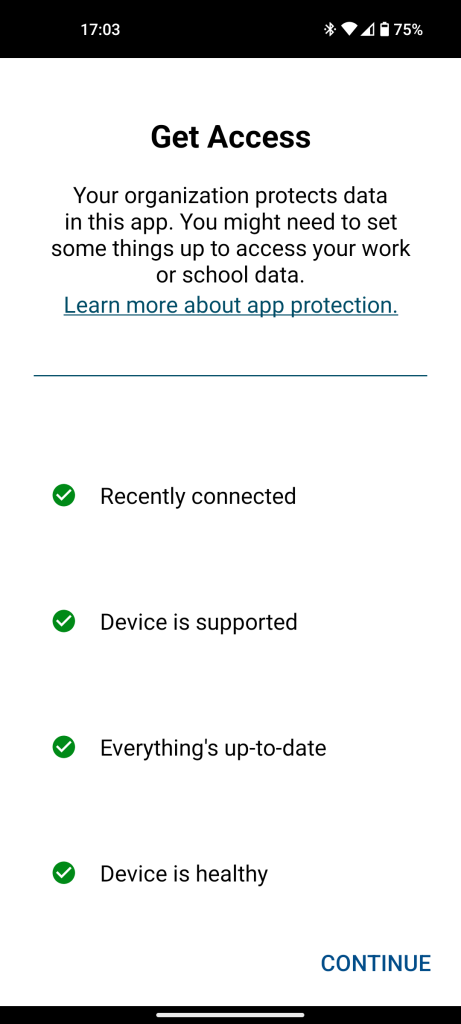
If any of these fail then the device will not work with org data anymore. Once you continue the user will be asked to register the device, this will register the device with AAD, so you can see the OS information, device compliance, etc, and use that for monitoring.
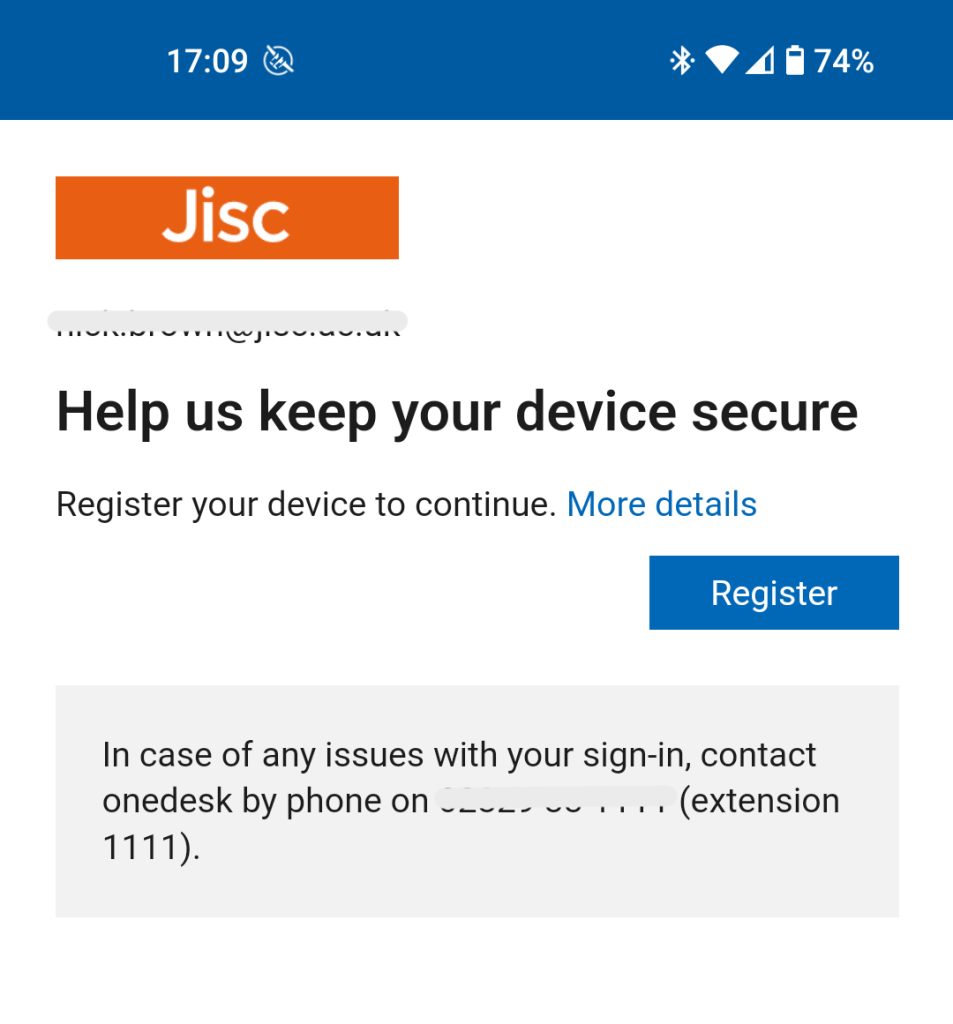
The user will be asked to configure a PIN during this setup process. Each time you load an app up it will check the state of the device and perform the actions you defined in the policy section.
Only then can you access the app and corporate data
This is a very long post, the next post I’ll go through more technical controls we have in place inside of Intune/AAD, Winget will be getting a big mention.

12 replies on “Road to Cyber Essentials: The Intune BYOD Controls”
Hi Nick,
Within our CE scope, we block access to BYOD currently, however we are investigating allowing BYOD mobiles. With company iOS devices we set the minimum point release, which is fairly easy as most devices support the latest iOS. However with Android currently maintained on v11 and above, do you have a recommendations as to how to increment the latest point release for each version? Or is this not a concern for Android?
Use the Security patch level instead for Android, this is released monthly but not all mans update their OS that often so go for something like 6 months, that should cover most. If they are outside of that you can take the OS as at risk
Hi Nick, great post – can you confirm if all this still applies following the recent Apple changes blocking Intune registration without managed Apple accounts? Also is all the above available with an A3 subscription?
Thanks in advance.
I believe on iOS now you don’t need the Intune app, the individual apps themselves do the registration. I’m not aware the managed apple requirement however.
And yes this is available with Intune Plan 1 (A3)
Doesn’t CE require that you also have to enforce restrictions at the device level as well? For example you can enforce 6 digit pins on apps, but CE requires 6 digits on the device itself. For that AFAIK that requires InTune with enrolment. Licensing then matters
Hi Barney, it does, at the time of writing the best you could do was ensure a PIN was used to access company data. On Android you can now require device level passcode complexity on the device as well as the app protection pin code. I would have that to medium or high.
We are in the same situation with BYOD blocked but now relaxing to allow some users access on mobile. We currently have “Users may join devices to Microsoft Entra” set to admins so we don’t get random devices added to Entra. Can this stay like this for BYOD to work or do we need to allow for the users we want to enrol devices?
Hi Robbie, as the instructions above say, allow devices to register with entra but block them from Intune enrolment. You should have devices registered in Entra for reporting purposes, but not in Intune. This avoids issues with tech’s accidently wiping a personal device but still having the devices in Intune for reporting purposes. For BYOD to work you need the entra registration stuff enabled.
When creating the MAM application protection policies for Android and IOS it seems you can no longer click “no” to target all devices” and the box to select “unmanaged” is greyed out? If you select no and save it is automatically selected as yes when you reopen the policy
Hi Robbie, you do that on the conditional access policy, not on the app protection policy, you can do if you want but you don’t need to. I would use the All Users options, not all devices, as you want to target users not intune devices
Confirming the conditional access will block them from Enrolling into Intune?
You’ll need to use Intune enrolment restrictions to stop that, I wouldn’t recommend using conditional access to block that