Jisc are Cyber Essentials compliant, this will be a series of blog posts on how we achieved this.
To start off you need to evaluate your digital estate, start small and expand from there. Your IdP will be your biggest asset in assisting with CE, make sure your systems use your IdP for login, try to avoid LDAP/Active Directory lookups.
Asset management plays a bit part of a Cyber Essentials submission, so you need some way of controlling/tracking who has access to what and on what device. We supplement our AAD with additional data around device warranty and device support dates scraping various internet sources for that information so it appears all in one place, more on that in a later blog post in this series.
To start, have a meeting with the stakeholders whom are needed for CE certification: this will include, but not limited to, IT technical leads; Senior Management; Data Protection Officers and any Cyber security specialists. Get around a table (virtually and/or physically) and talk, CE is not something that can be implemented in a silo.
The biggest first step is MFA, get everyone on MFA ASAP.
If you haven’t implemented MFA here are a few basic steps (note I’m a 365 Architect so that’s where this will be aimed at):
- Enable combined security information registration
This enables the new modern MFA setup process (this will be the default as 30th Sept 2022) - Disable SMS and enable voice based MFA. For MFD’s and akin you may also want to enable Certificate based MFA.
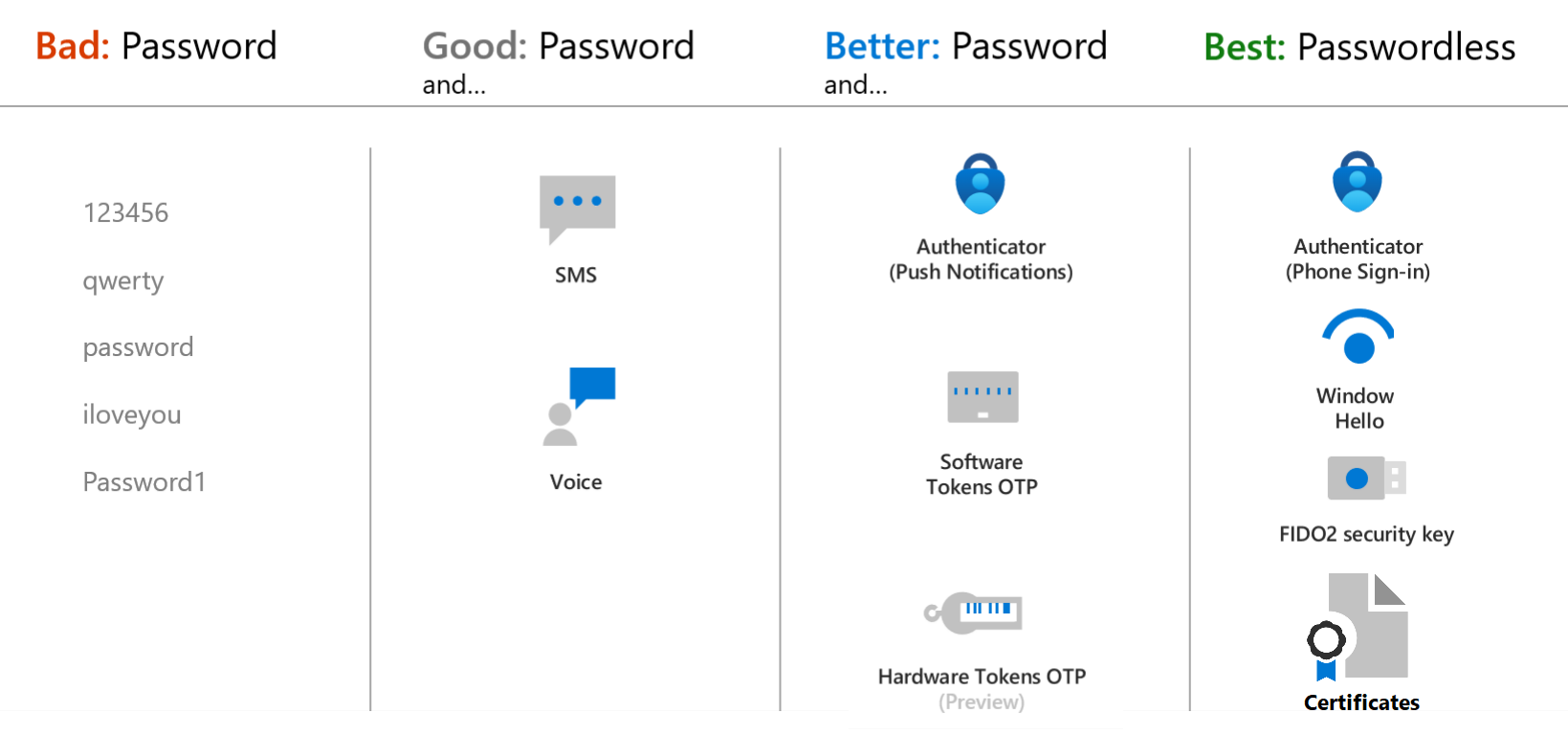
- You can then either do custom policies or
- Enable Security Defaults
This will configure the above, but not allow you to change or reconfigure them - Custom Policies
- Configure an MFA Registration Campaign
Give your users 14 days or so to register for MFA prior to enforcing MFA via Policy - Configure common Conditional Access Policies.
I would recommend the Block Legacy Auth and Require MFA for all users policy, however you may want to start with admins first.
If you are A3 you can then customize these CAPs
- Configure an MFA Registration Campaign
- Enable Security Defaults
In future blog posts we’ll go into the written policies as well as technical controls.
If you need any assistance with anything discussed in this post please feel free to reach out to your Jisc Relationship Manager.
