This is the second in the Road to CE series of blog posts following Jisc’s full Cyber Essentials journey.
In this part of our journey, we had a meeting with senior stakeholders as well as our IT Security teams, explored the requirements for Cyber Essentials and how best to achieve those for Jisc and scoping initially to a smaller team. You will be reviewing your written policies, which we will cover in the next post in this series.
For the initial pilot group you will want a mixture of technical competencies which best cover your organisation. We opted for Cloud as we have very technically competent team members and administrative staff who aren’t as technically competent.
If you are going to put the pilot group through Cyber Essentials certification with an assessor, you must use MAC address VLAN isolation, even if you users aren’t accessing internal on-premise resources, just internet resources, this may catch you out so be aware. You can’t do user based VLAN isolation it must be MAC address filtering. Get your networking team involved if you are performing a scoped assessment.
During this phase we discovered how much, or little, change was needed both to technical control and written policy. The big take away for schools/colleges/universities is students are out of scope for Cyber Essentials. However, if those students are Post-Grad Researcher students, I would classify them as staff and you should treat them as such, meaning they are in scope for CE.
You will need to at least update your written policies into a draft state to reinforce the technical controls/limitations you are imposing on staff. We will discuss policy more in the next blog post.
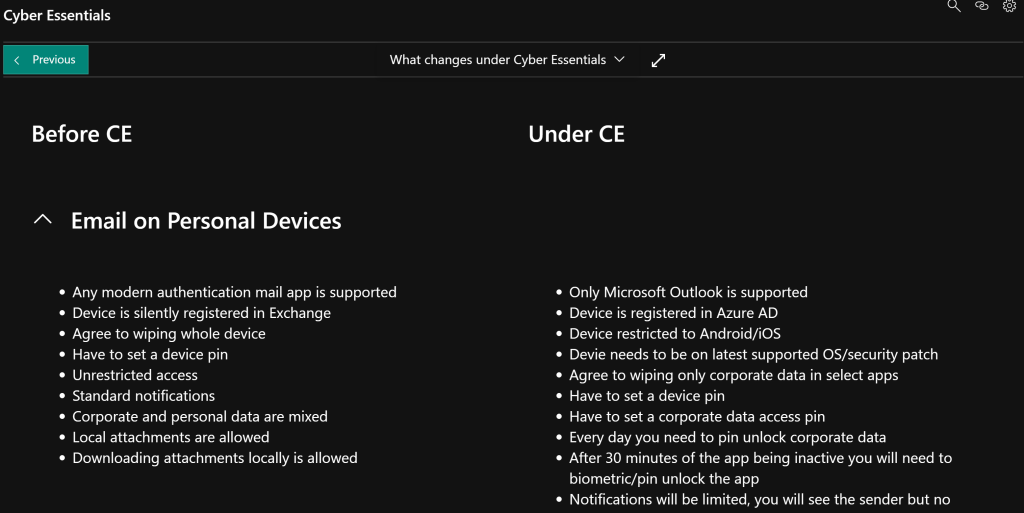
We decided on quite a restrictive policy: OneDrive/Outlook/SharePoint/Teams would be the only 365 apps available for BYOD and that BYOD will be restricted to iOS and Android. Managed devices Intune compliance policies will be expanded/replaced/updated. We also elected to move devices into non-compliance within 3 days of updates, requiring devices are updated before normal operation resumes. Password requirements already exceeded Cyber Essentials but pin requirements for BYOD needed to be increased.
In January 2023 model support was dropped as a requirement for Cyber Essentials, this makes implementing technical controls (future series post) easier, especially in Intune, however we strongly recommend have a set device replacement schedule in place to avoid hardware level vulnerabilities which cannot be fixed by a OS/firmware patch.
For Mac/iOS you can rely on the OS version, as Apple will deprecate devices by removing support for the OS. For Android things get very tricky, we went with a supported Android OS (11 as of the time of writing) and a max of 3 months old security patch. For Windows we permit any supported OS build of Windows 10/11, with build number compliance policies. We elected not permit Windows/Mac BYOD under CE.
You could get staff to fill a form in with device details and verify they are using up to date devices, however if you are able to show you have technical controls in place as well as written policies assessors will rate that more favourable. You can get a few non-compliance sections in you Cyber Essentials assessment, however the less the better.
Keep things moving during the pilot phase, start with initial comms to the pilot group informing the of the changes coming to their devices. We created a SharePoint site with information on Cyber Essentials, complete with what will change on their devices, once the pilot was completed this information was Jisc’ified and modified more for the wider org.
Start promoting updated policies with the pilot group prior to implementing the technical controls, these policies can still be in ‘draft’ format, they will need to be finalised for assessment.
Under Cyber Essentials administrative tasks need to be performed on separate ‘admin’ accounts, these should not be used for day-to-day tasks. If you are using Privileged Identity Management (PIM) you will need to use this on separate admin accounts, you cannot have PIM on standard (day-to-day) accounts, that is deemed a non-compliance under Cyber Essentials. We recommend that even device admin accounts, used to install software, are avoid where possible, they should be centrally managed for password compliance at least. Under Cyber Essentials admin accounts should ideally be firewalled to prevent internet access, however this isn’t normally practicable, ensure there is written policy stipulating how and when to use admin accounts.
Audit the pilot group, find out what applications and services they are using/administering/providing and log these. Check these applications are using MFA, ideally using you IdP with SSO to avoid user fatigue and improving automated risk. You will report these applications during your Cyber Essentials assessment and show how you keep these apps up to date/secure.
Your IdP/MDM will show its benefits during Cyber Essentials.
Some users, even in the pilot group, will not want corporate control on their personal devices, even if it’s light touch application level control, in this case those devices should be blocked and corporate devices issued, this will involve capital expense. You should weigh up that expense against the fines from the ICO (or other body) for a data breach (The maximum fine the ICO can issue is £17.5 million, or 4% of a company’s total worldwide annual turnover, whichever is higher), ransomware ransom pay-out, or even reputation damage.
The Education sector is the biggest target for cyber attacks, so take a secure first approach.
Your pilot users will be key to ensuring a smooth rollout of Cyber Essentials and the policy & technical changes that will come with it. Use them to get applications packaged and centrally deployed, adjust security policies, update your draft written policies and reword/tweak the comms that will be used for the end users.
Since members of the cloud team were also those adjusting technical controls/assisting with policy rewrites this greatly increased the efficiency of the deployment.
Next in the Road to CE series I’ll talk about the written policies, what you may/may not want to include and we’ll look at what in Jisc we changed for Cyber Essentials and other security enhancements. After that will be technical controls inside of Intune so stay tuned.