This is the 7th part of my blog series on the Road to CE series. In today’s post we’ll look at Defender for Identity and Azure Identity Protection to assist with Cyber Essentials.
One big area in Cyber Essentials is monitoring and removing access when a compromise occurs, Microsoft has tools built into Azure AD and enhanced AV features for endpoints to protect identities and provide additional security, automated monitoring and more.
I’ll be assuming that you are using Azure AD as your primary IdP (Identity Platform), these features will be severely limited if you are not using AAD as your primary IdP, Microsoft will use all of the sign-in data from the IdP as well as external processes and data to monitor Identities to pick up abnormalities. Defender for Identity will monitor your endpoints and even Active Directory to combine these factors into AAD.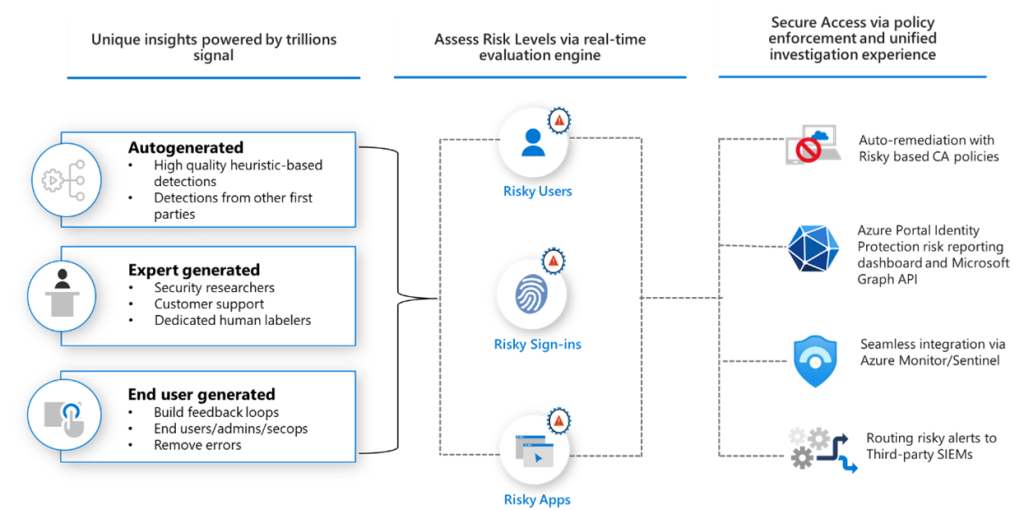 You use Conditional Access Policies to enforce AAD IP, this is exposed as Sign in Risk and User Risk levels. Microsoft even has templates for this. Be aware user sign in risk is an Azure AD P2 feature (A5/E5).
You use Conditional Access Policies to enforce AAD IP, this is exposed as Sign in Risk and User Risk levels. Microsoft even has templates for this. Be aware user sign in risk is an Azure AD P2 feature (A5/E5).
Open Conditional Access – Microsoft Azure and select New Policy, set it for all users and all client apps.
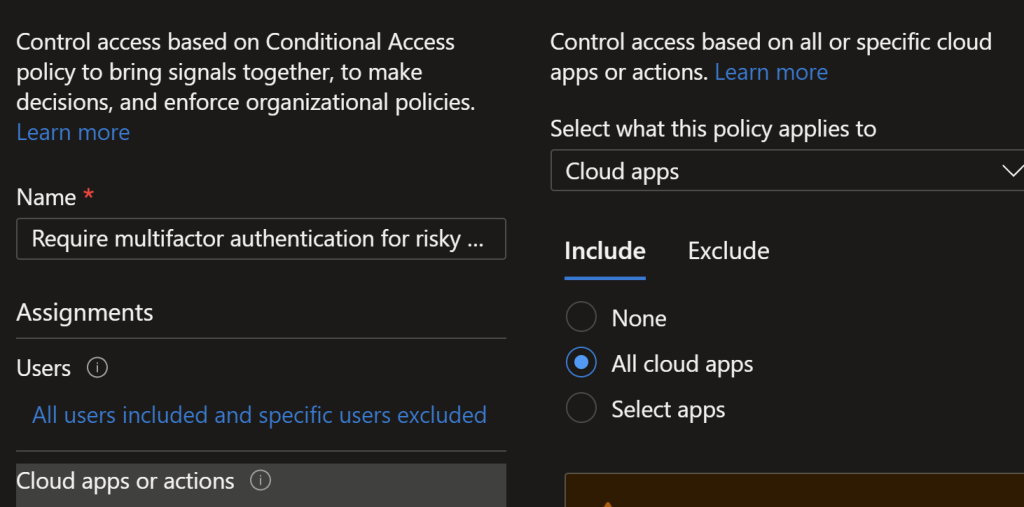
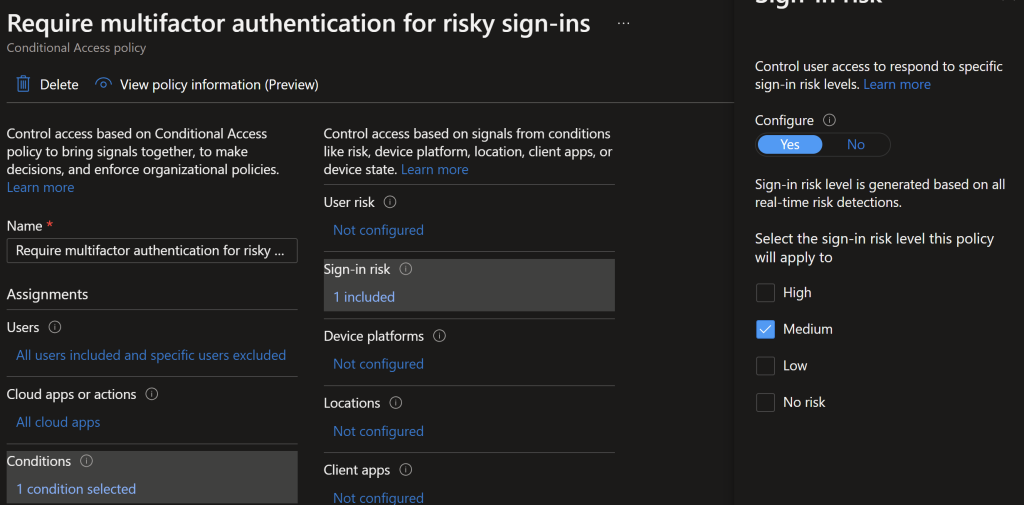
Select the condition of user risk/sign in risk of medium
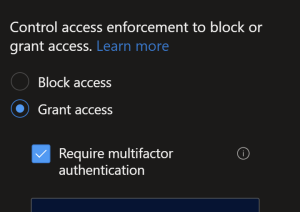
Under grant select Grant Access > Require MFA
Under session control set to remove persistence and a session timeout straight away, once the risk drops down persistence will come back on.
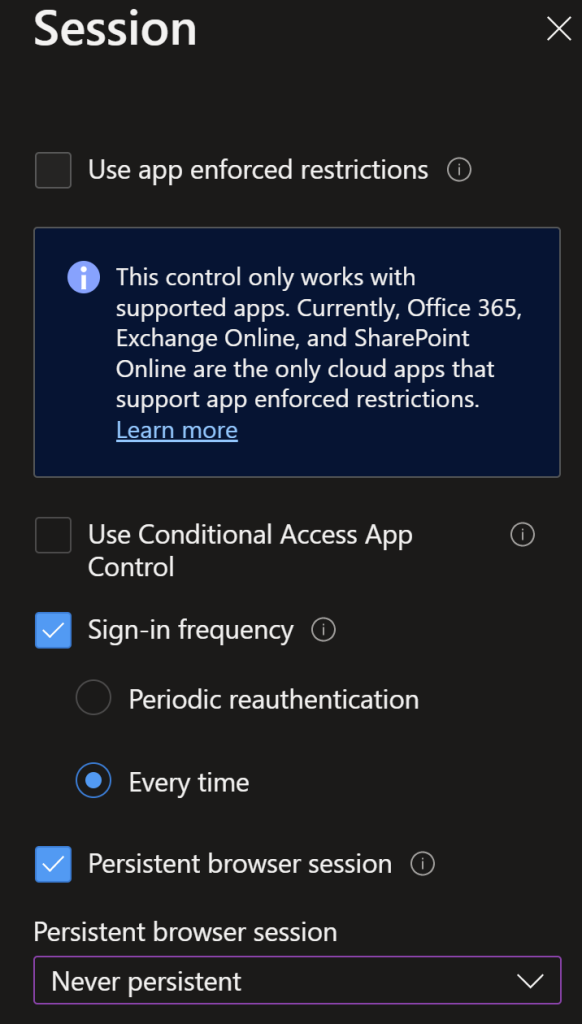
Once that is done create another policy for User Risk Medium.
High User Risk
We have gone down the route of user/sign in risk high block access. To do this, create 2 new policies, 1 for user risk and one for sign in risk of high. Set the grant to block. You don’t need a session control as block is in it self a session control.
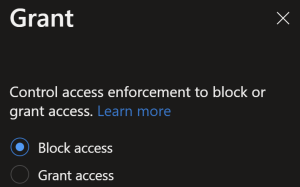
That turns on Azure AD Identity Protection, next we’ll look at Defender for Identity.
Defender for Identity
Defender for Identity runs on your Active Directory Domain Controllers and passes sign-in information upto Azure AD to enhance the protection. Follow the installation guide at Deploying with Microsoft 365 Defender – Microsoft Defender for Identity | Microsoft Learn.
Endpoint Security Account Protection
You can configure Windows/Defender to monitor passwords on the endpoints and alert to security breaches.
Go to Endpoint security – Microsoft Intune admin center. Create a new Account Protection Policy. Turn on Credential Guard and Enable to use enhanced anti-spoofing, when available. We would also recommend in a standard policy (talk about that next week) to enforce password protection in edge.
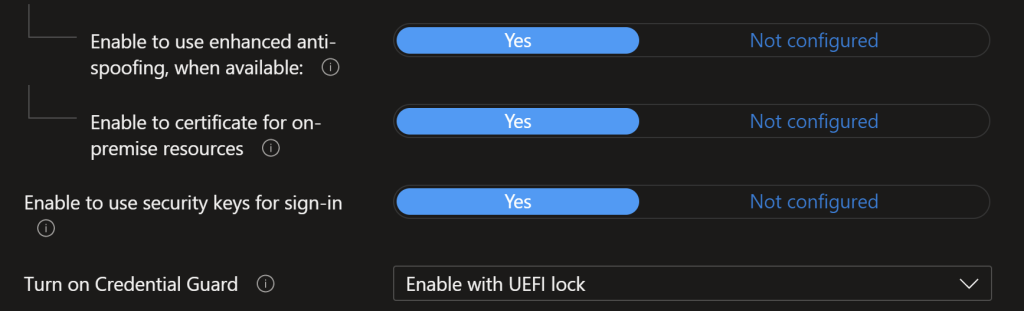
That completes this post on the Road to CE series. More Intune/AAD Technical Controls to come.

2 replies on “Road to Cyber Essentials: Defender for Identity/Azure Identity Protection”
Thanks for the series.
You may need to mention that sign in risk needs an Azure P2 license.
Good spot, added a line that it’s a P2 feature