This is the 8th part of my Road to CE series, in this post we’ll look at Android and fully managing Android.
Microsoft + Android MDM is a lot easier than Apple, that’ll be coming up in the next post.
Initial Setup
First follow the instructions on Connect your Intune account to your Managed Google Play account. – Microsoft Intune | Microsoft Learn to establish the connection to Google’s services. As the documents says you can either use any gsuite account or a generic account for IT.
Once set up comes the fun, if you don’t want to go down the zero touch route for Android devices (similar to Apple Business Manager) you can use Token enrolment, where you type in a code and scan a QR code to enrol the device prior to issuing to a user.
Enrolment
Microsoft’s learn articles will assist you with this process massively: Set up enrollment for Android Enterprise fully managed devices – Microsoft Intune | Microsoft Learn.
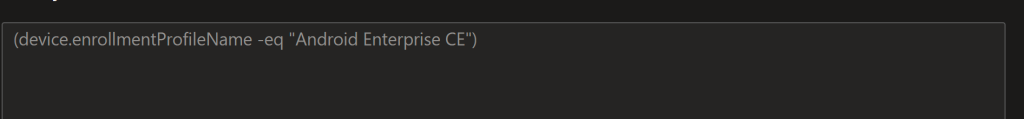
The dynamic group for devices using the enrolment profile name will come in handy later. I also recommend creating a Tenant Filter as well. Tenant Administration > Filters > Create > Android > enrollmentProfileName = name of the profile you created above. Using filters means you can use All Users/All Devices instead of a dynamic group, very useful if you are doing your whole org at once.
To enrol devices you then follow the instructions at Enroll Android Enterprise dedicated, fully managed, or corporate-owned work profile devices in Intune – Microsoft Intune | Microsoft Learn. We used the Token enrolment method. This enrols the device in Intune after which it will restart and you can hand the device to the end user. The device will be fully managed via Intune and AAD credentials.
The one issue with Android is a device naming policy isn’t available, so you’ll need to trigger a rename via Intune. The Jisc CE/M365 Tool will have built in functionality to trigger a device rename for Android to match your other naming scheme.
Compliance Policy
Create a new Compliance Policy for Android to avoid any conflicts. If you are using the Jisc CE/M365 Tool you’ll put Cyber Essentials into the description to get Android version information auto updated.
For fully managed devices I’ll talk though an example of what I recommend setup: Deploy Defender to managed devices so you can set defender’s requirements to be clear and secured. The Jisc CE/M365 Tool will update the Min OS and patch levels automatically, they are set to the min supported Android version and today – 3 months for security updates, you can manually update these settings.
This will cover most devices and ensure they are kept up to date.
For CE compliance I recommend marking devices as noncompliant after 1 day, retire the device after 14 days and lock the device after 7 days, this should match your Apple/Windows compliance and CE policies.
Configuration Profile
Configuration will mostly follow your companies requirements but this is the basics from our demo tenant
General
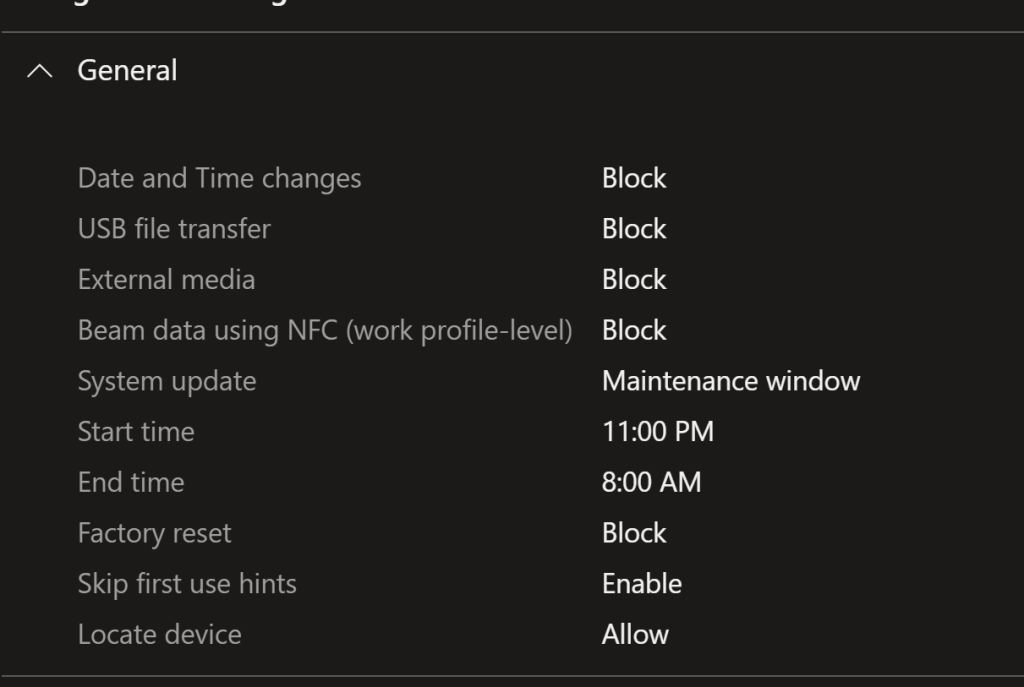
Here block Date/Time changes, USB file transfers and external media, this is a mainly my recommendation but NCSC suggest setting it for improved security. I recommend specifying the maintenance window to avoid androids resetting during normal working hours. Factory resets are handled by Intune so we block them for the end user.
System security/device experience
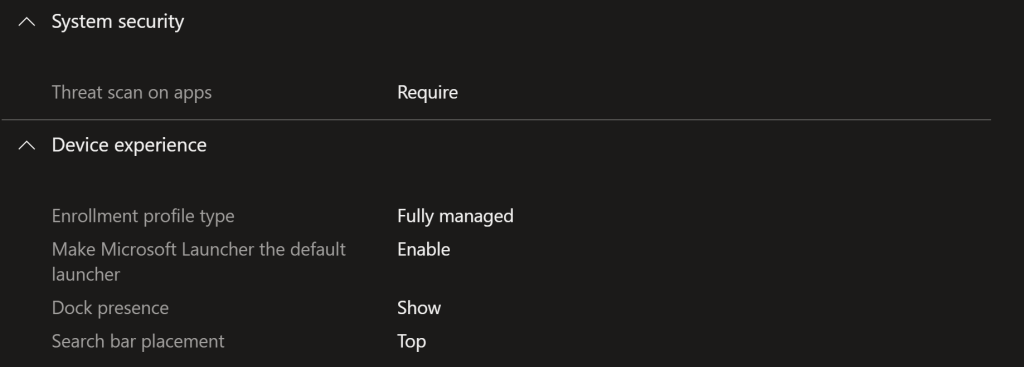
I would strongly set “require threat scan” on apps, putting the device into fully managed mode, making Microsoft Launcher the default, allowing dock and specifying the search bar placement. Device experience is mainly org preference but I don’t find the Microsoft Launcher an issue, I actually use it personally but I’m a Microsoftie.
Device password/User accounts
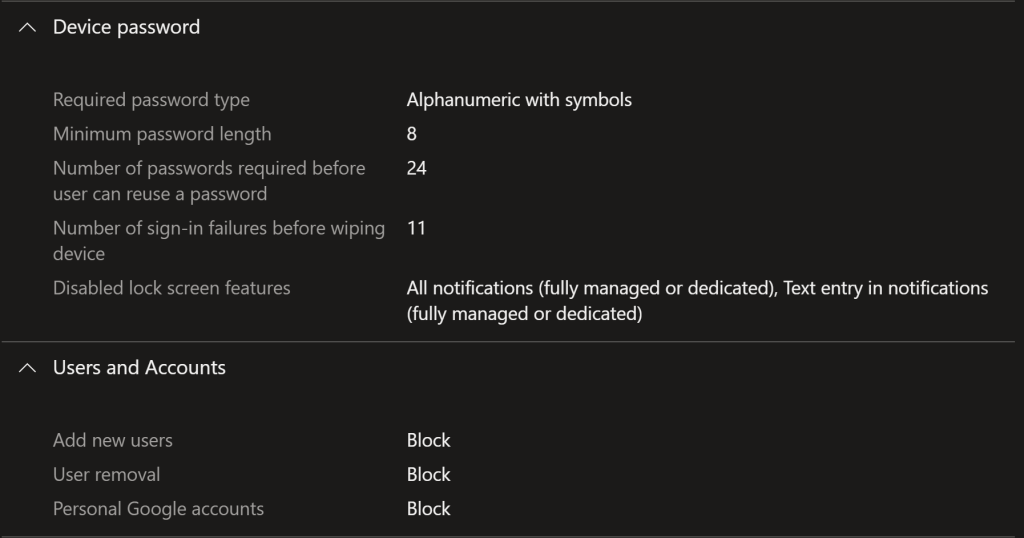
For device password, we duplicate the settings we used in the compliance policy (to avoid conflicts), additional disabling lock screen notifications to avoid Data Leakage. For users and accounts we block adding/removing accounts and personal google accounts. If you want to allow personal usage on a corporate phone you could allow adding/removing/Google accounts here to use the Work profiles, but we are keeping it simple.
Other Settings
The only other setting I suggest having is to only use Wi-Fi for updates, this is purely a way to avoid unwanted mobile data usage, but you may feel differently.
Apps
Because you have linked to a managed Google account you can use Intune to acquire and publish apps from the Google Play. Intune > Apps > Android > Add > Managed Google Play app.
You will be presented with the Google Play store where you find and select the app you want. After you approve the app you then click Sync, the app should show up in the app list for your to push to users/make available.
I would recommend making required:
- Microsoft Defender
- Intune Company Portal
- Microsoft Launcher
- Microsoft Authenticator
- Microsoft OneDrive
- geteduroam
- Other Microsoft apps (Teams)
Closing
Android managed is a lot easier, and less clicks than Apple management and in some cases easier than Windows. I hope these slightly omitted instructions can help you with your Intune journey to CE compliance.
Come back soon for more on the Road to CE, until next time, stay safe and secure!
